How to retrieve a LDAPS certificate
This article describes 3 methods of obtaining the LDAPS certificate from the Active Directory (AD) Server that is active in your deployment, to then install on the PCoIP Management Console. This will allow the LDAPS connection between products that require Active Directory for authentication, such as PCoIP Management Console or HP Anyware Manager, and the Active Directory Server to successfully establish.
Using OpenSSL on Any Platform to Create the LDAPS Certificate from the AD Server
Using OpenSSL should work with any Active Directory Server platform. (Windows, Linux etc.). The example below, uses OpenSSL 1.1.0h 27 Mar 2018. If having difficulties using another version of OpenSSL, consult the appropriate OpenSSL documentation.
Requirements:
- Openssl
- FQDN or IP of the Active Directory Server
- LDAPS certificate installed in the Active Directory Server certificate store
Steps:
- Run the following command from your local computer:
openssl s_client -showcerts -connect <ip or fqdn of your active directory server>:636 - In the output, copy the certificate portion of the output to a text file
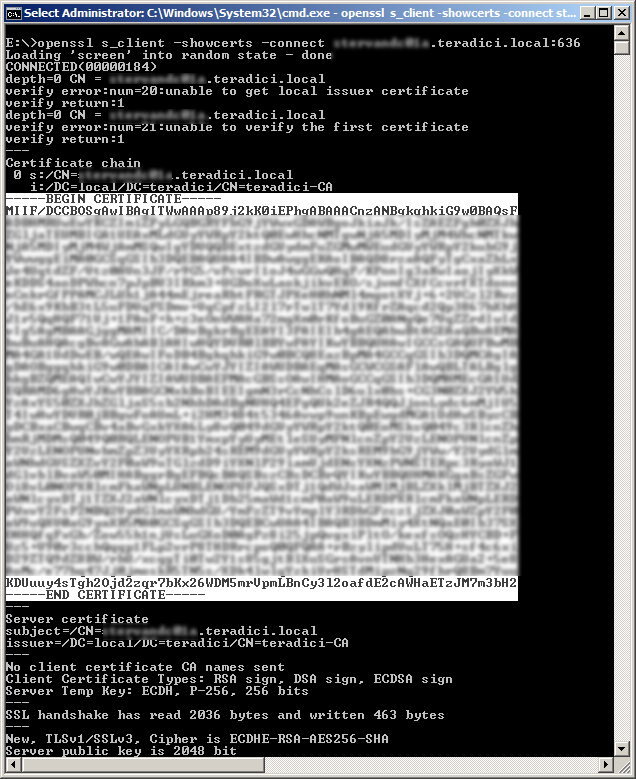
3. Save the text file as my_ldaps_cert.pem.
The saved certificate can be installed into any software that needs to connect to your Active Directory using LDAPS.
Using Openssl on a Linux Platform to obtain the LDAPS certificate from the AD server
Requirements:
- Openssl installed on your Linux computer
- FQDN or IP of the Active Directory Server
- LDAPS certificate installed in the Active Directory Server certificate store
Perform the following steps:
- Enter the following command from your Linux computer:
openssl s_client -showcerts -connect <fqdn of your ldap server>:636 -servername < fqdn of your ldap server> </d ev/null 2>/dev/null > my_ldaps_cert.pemExample:
openssl s_client -showcerts -connect mydc.mycompany.com:636 -servername mydc.mycompany.com </d ev/null 2>/dev/null > my_ldaps_cert.pem - Upload my_ldaps_cert.pem to the PCoIP Management Console. See Installing an Active Directory Certificate in the PCoIP Management Console Administrators' Guide.
The saved certificate can be installed into any software that needs to connect to your Active Directory using LDAPS.
Obtaining the LDAPS Certificate from the Active Directory Server
The example below has been successfully tried on both Windows 2008 R2 and Windows 2016 Active Directory servers. Consult with your Active Directory documentation for official methods on obtaining the LDAPs certificate for use in your deployment.
Requirements:
- FQDN or IP of the Active Directory Server
- Administrator username and password of the Active Directory Server
- LDAPS certificate installed in the Active Directory Server certificate store
Perform the following steps:
- On the Active Directory Server, login as administrator.
- Launch mmc.exe.
- From the Console, click on File > Add/Remove Snap-in
- In the Add or Remove Snap-ins, select Certificates, then click Add.
- In the Certificates snap in dialog box, select Computer account, and click Next.
- In the Select Computer dialog, select Local computer: (the computer this console is running on), then click Finish.
- In the Add or Remove Snap-ins window, click OK.
- In the Console, in the left pane, browse to Certificates (Local Computer) > Personal > Certificates. Choose the correct LDAPS certificate. This is the certificate with the following information:
- Issued To: <the fqdn of your LDAP server>
- Issued By: <The Certificate Authority where your admin requested the certificate from>
- Right-click on the certificate and click All Tasks > Export.
- In the Certificate Export Wizard, do the following:
- Select not to export the private key
- Choose Base-64 encoded X.509 file format
- Save the certificate as my_ldaps_cert.pem.
The saved certificate can be installed into any software that needs to connect to your Active Directory using LDAPS.