How to disable Trace in PCoIP Management Console
When running a scan against PCoIP Management Console you may find that it is flagged for the TRACE vulnerability.
This is due to a change in the Jetty package used with Management Console. To rectify this issue, you will need to modify the webdefault.xml file located in /opt/jetty/etc.
The procedures to fix this issue are different depending on which Management Console version you are using.
- For Management Console 3.x
- For Management Console 19.05 and higher
- Management Console 22.09 and higher
For Management Console 3.x
Before modifying the webdefault.xml file you can confirm the vulnerability by executing the command :curl -i -k -X TRACE https://10.0.171.112/console/
Example:
[root@localhost ~]# curl -i -k -X TRACE https://10.0.171.112/console/
HTTP/1.1 200 OK
Content-Type: message/http
Content-Length: 111
Server: Jetty(9.3.25.v20180904)
TRACE /console/grails/login/index.dispatch HTTP/1.1
User-Agent: curl/7.29.0
Accept: */*
Host: 10.0.171.112
[root@localhost ~]#
To fix the issue, edit the webdefault.xml file by replacing the string <url-pattern>/</url-pattern> with <url-pattern>/*</url-pattern>.
- Open a text editor such as VI or VIM.
- Navigate to the /opt/jetty/etc directory
- Edit the webdefault.xml file. As an example, if using VI you would enter the following command:
vi webdefault.xml - Scroll to the bottom of file and replace the line
<url-pattern>/</url-pattern>
with
<url-pattern>/*</url-pattern> - Save your changes and exit the editor.
The webdefault.xml should now have the corrected entry.
<!-- ==================================================================== -->
<!-- Disable TRACE method with security constraint -->
<!-- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -->
<security-constraint>
<web-resource-collection>
<web-resource-name>Disable TRACE</web-resource-name>
<url-pattern>/*</url-pattern>
<http-method>TRACE</http-method>
</web-resource-collection>
<auth-constraint/>
</security-constraint>
<security-constraint>
<web-resource-collection>
<web-resource-name>Enable everything but TRACE</web-resource-name>
<url-pattern>/</url-pattern>
<http-method-omission>TRACE</http-method-omission>
</web-resource-collection>
</security-constraint>
</web-app>
After modifying the webdefault.xml file you can test your changes by issuing the command: curl -i -k -X TRACE https://10.0.171.112/console/
Example:
[root@localhost ~]# curl -i -k -X TRACE https://10.0.171.112/console/
HTTP/1.1 403 Forbidden
Content-Length: 0
Server: Jetty(9.3.25.v20180904)
[root@localhost ~]#
For Management Console 19.05 and higher
- Configure Jetty Trace and Options by using below steps
- SSH to Management Console server using an SSH client such as PuTTY.
- Navigate to the config folder by issuing the following command:
cd opt/teradici/console/config - Open mc-external-config.yml for editing such as Vi.
sudo vi mc-external-config.yml - Un-comment the following Jetty parameters and ensure the traceEnabled and optionsEnabled parameters to false.
From:
# jetty:
# port: 8080
# sendServerVersion: false
# hsts:
# enableHSTS: false
# stsMaxAge: 3153600
# traceEnabled: false
# optionsEnabled: false
To:
jetty:
port: 8080
sendServerVersion: false
hsts:
enableHSTS: false
stsMaxAge: 3153600
traceEnabled: false
optionsEnabled: false - Save the mc-external-config.yml file by selecting the Esc key then typing in :wq and selecting the Enter key.
Restart Management Console by issuing the following command:
sudo systemctl restart mcconsole
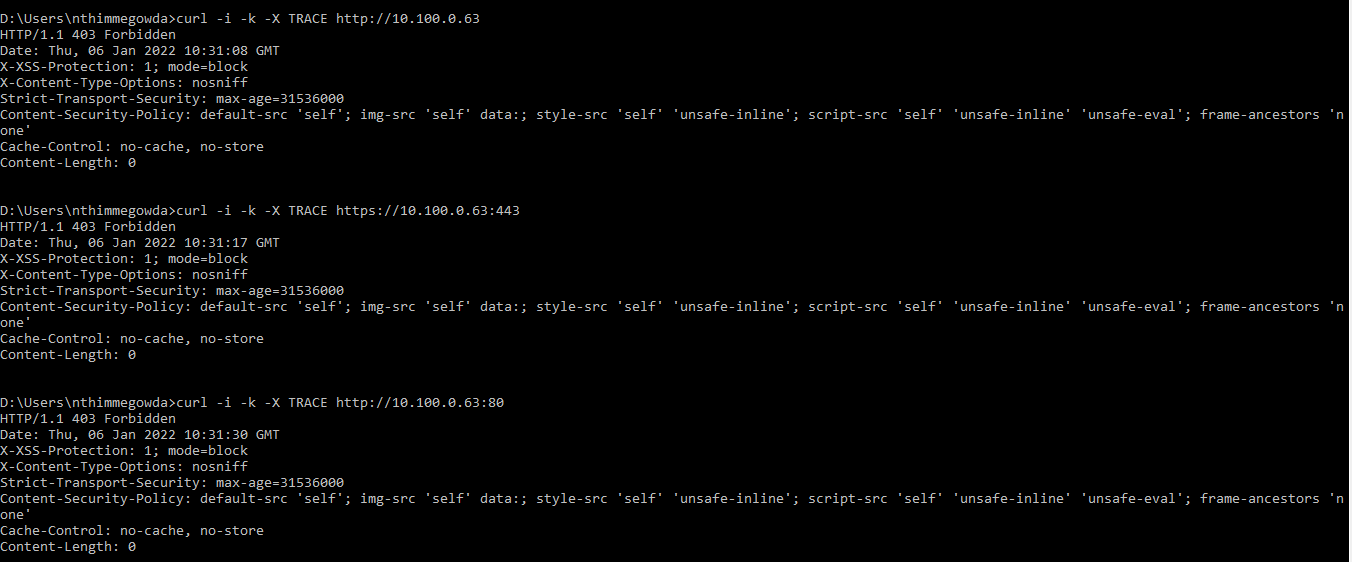
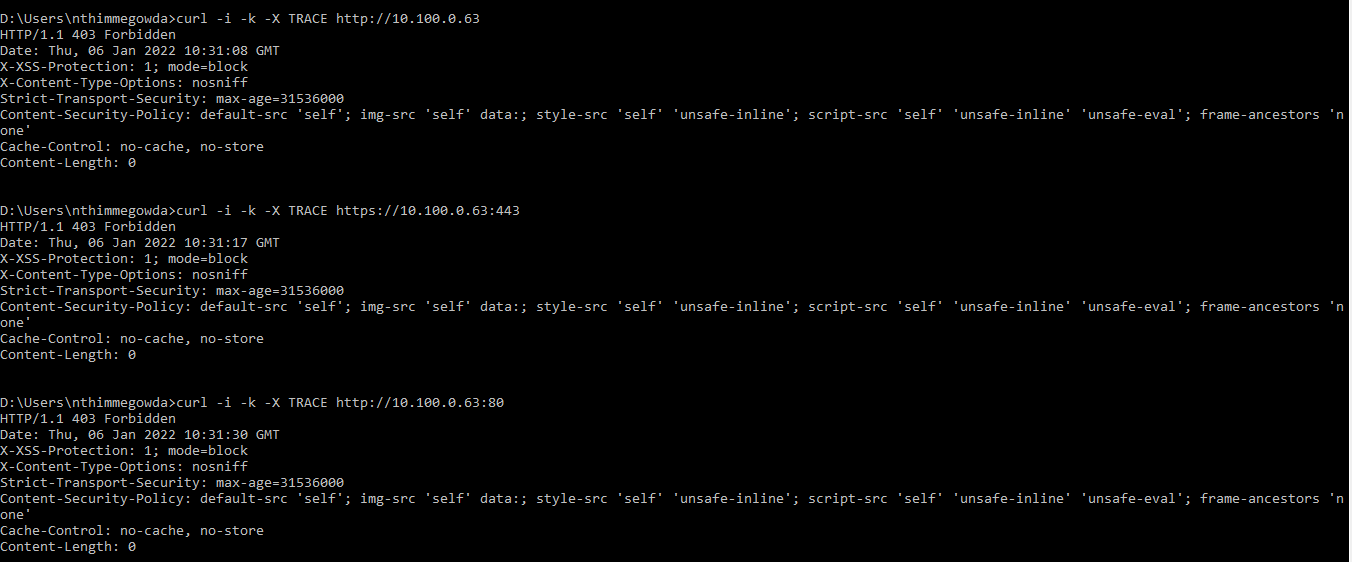
2. Check the trace functionality from the Management Console virtual console.
- Open the Command prompt.
- Enter one of the following curl commands:
Example Output
curl -i -k -X TRACE https://<Management Console IP Address>/ curl -i -k -X TRACE http://<Management Console IP Address>/ curl -i -k -X TRACE https://<Management Console IP Address>/dashboard curl -i -k -X TRACE https//<Management Console IP Address>:<Port Number>
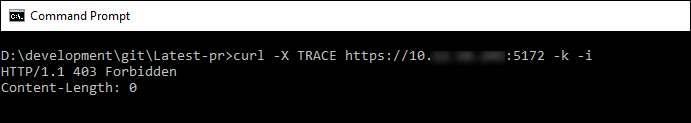
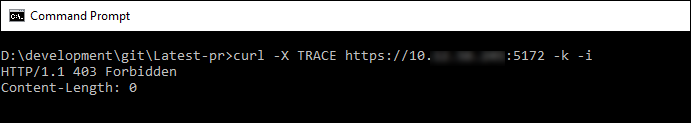
For Management Console 22.09 and higher
cd /opt/teradici/scripts
./set_port_external.sh TRACE DISABLE
sudo systemctl restart mcdaemon
curl -i -k -X TRACE https://<Management Console IP Address>:5172
Example Output